Preventing Confidentiality Incidents: New CAI Guidance

Preventing confidentiality incidents (i.e., the term used under Quebec law for privacy breaches) is not only a legal obligation in Quebec, but also an essential component of sound risk management and corporate governance. On January 30, 2026, Quebec’s privacy regulator, the Commission d’accès à l’information (“CAI”), published new guidance on the prevention of confidentiality incidents, including a step‑by‑step Guide that sets out the CAI’s prevention approach and a complementary Checklist intended to help operationalize it.
Released as part of Data Protection Week 2026, the guidance provides operational direction for businesses subject to Quebec’s private-sector privacy law, the Act respecting the protection of personal information in the private sector (“Private Sector Act”). Note that the guidance is only available in French.
The legal framework
Security safeguards
Article 10 of the Private Sector Act imposes a foundational obligation on every organization carrying on an enterprise in Quebec: it must take security measures necessary to ensure the protection of personal information that are reasonable in light of the sensitivity of the information, its purposes of use, its quantity and distribution, and the medium on which it is stored. This obligation applies across the entire lifecycle of personal information, from collection to destruction or anonymization.
Importantly, article 10 is not limited to information‑technology controls. It requires a broader, risk‑based approach that combines administrative (governance), physical, and technical measures.
Confidentiality incidents and breach response
Organizations subject to the Private Sector Act also have express statutory obligations when a confidentiality incident occurs. An incident exists where personal information is accessed, used, or communicated without authorization, or where it is lost or that its protection is otherwise breached.
When an organization has cause to believe such an incident has occurred, it must:
- take reasonable measures to reduce the risk of injury and prevent similar incidents;
- assess whether the incident presents a risk of “serious injury” to the individuals concerned;
- report the incident to the CAI and notify affected individuals if that threshold is met; and
- maintain a register of all confidentiality incidents, regardless of severity.
These obligations operate in parallel with the preventive duty in article 10: weak safeguards can lead to incidents, and inadequate incident handling can independently constitute non‑compliance with the Private Sector Act.
Fines and penalties
Failure to comply with either set of obligations can attract significant consequences. Monetary administrative penalties or penal fines may be imposed, notably for: (i) failing to take necessary security safeguards (a breach of article 10 of the Private Sector Act); or (ii) failing to report or properly manage a confidentiality incident as required by articles 3.5 to 3.8 of the Private Sector Act[1]. In addition, where an offence is committed by a legal person, administrators, directors, or representatives who ordered, authorized, or consented to the offence may themselves be held liable to the prescribed penalties[2].
For organizations, monetary administrative penalties can reach the greater of $10 million or 2% of worldwide turnover, while penal fines can reach the greater of $25 million or 4% of worldwide turnover – and said penal fines can be doubled for repeat offences[3]. Even absent any publicly available precedents imposing fines to date, organizations should be acting now to mitigate foreseeable enforcement risk and mitigate reputational damages resulting from non-compliance. In that context, practical guidance on preventing confidentiality incidents is particularly timely.
Key takeaways from the guidance
Baselining on what a confidentiality incident is
The Guide begins by clearly baselining what constitutes a confidentiality incident under the Private Sector Act. It emphasizes that incidents extend well beyond headline‑grabbing cyberattacks. Everyday operational failures – misdirected communications, unauthorized access to personal data, human error, and third-party intrusions – can all qualify.
This framing is important because it reinforces that incident prevention is an organization‑wide responsibility, not solely an IT or cybersecurity issue.
Privacy protection vs. IT security
The Guide addresses the relationship between privacy protection and information‑technology security, emphasizing that while the two are complementary, they are not synonymous. By way of example, an organization may deploy a highly secure technical solution – such as encrypted systems or secure forms – yet still trigger a confidentiality incident if an employee sends personal information to an unauthorized recipient. Strong IT security does not, on its own, ensure compliance with privacy law.
The seven‑step prevention framework
At the core of the Guide is a seven‑step prevention framework, which the CAI presents as a continuous risk‑management cycle rather than a one‑time exercise.
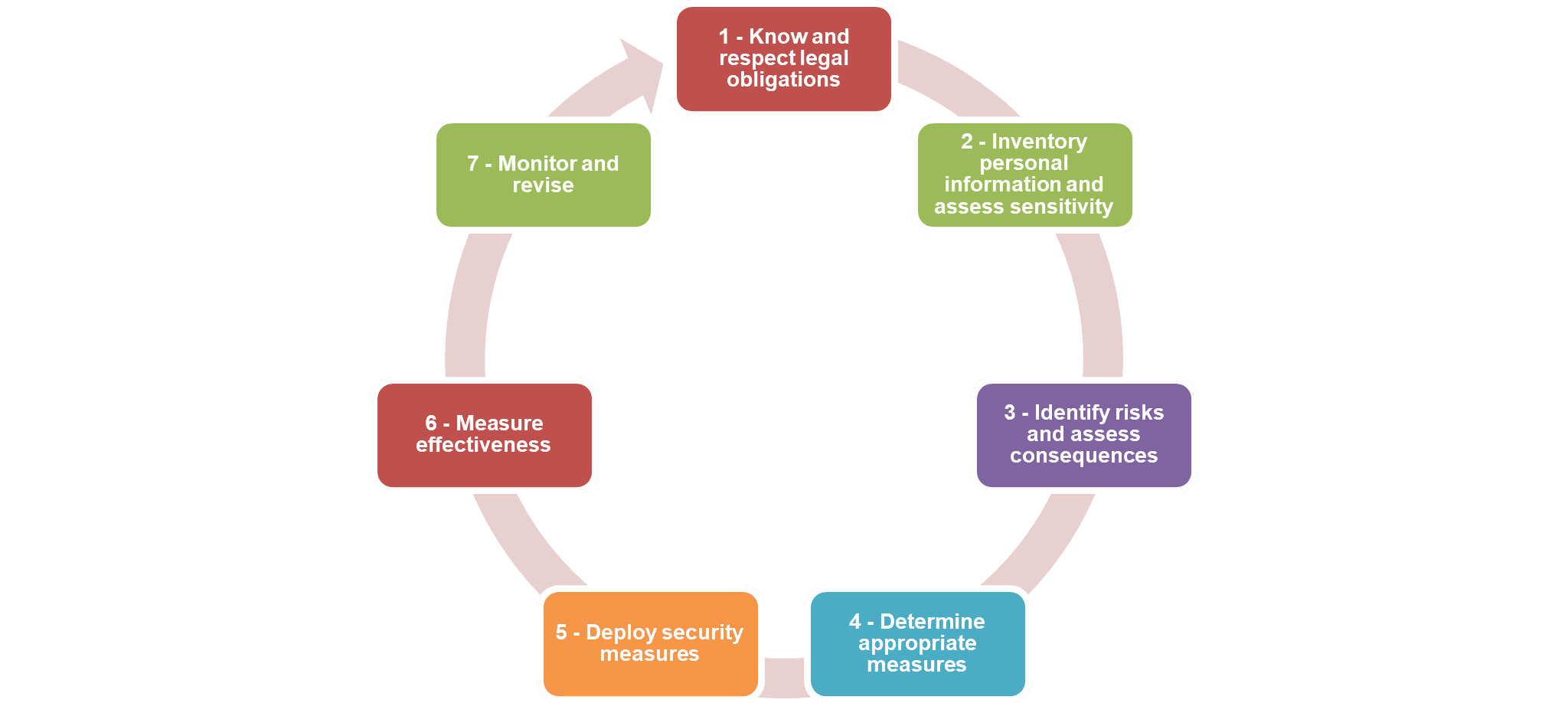
The above is our unofficial English translation of the chart found on page 5 of the Guide.
The seven steps are summarised below.
- Know and respect legal obligations – ensuring that governance, roles, and core privacy principles are understood and applied.
- Inventory personal information and assess sensitivity – documenting what personal information is held, for what purposes, by whom, where it is stored, and how sensitive it is.
- Identify risks and assess consequences – analysing reasonably foreseeable risks, their causes, likelihood, and potential impacts on individuals.
- Determine appropriate measures – selecting administrative, physical, and technical controls that are proportionate to the identified risks.
- Deploy security measures – implementing those controls with clear leadership support, planning, and communication.
- Measure effectiveness – evaluating whether measures work as intended and adjusting risk assessments accordingly.
- Monitor and revise – continuously updating practices in light of evolving threats, technologies, and organizational changes.
The Guide unpacks each step in detail and illustrates how they build on one another. The Checklist builds on these principles by proposing a series of concrete steps that organizations can take to implement them effectively.
Unpacking the inventory recommendation (Step 2)
Step 2 of the Guide centres on inventorying personal information and documenting its context of processing, including purposes, sensitivity, access controls, retention periods, storage locations, and transfers. Read as a whole, the Guide frames this inventorying exercise as a core building block of an organization’s privacy‑risk‑management strategy, enabling meaningful identification of confidentiality risks and the implementation of proportionate safeguards.
The Guide expressly situates this inventorying exercise alongside privacy impact assessments (“PIAs”), which are already required under articles 3.3 (information systems projects) and 17 (cross‑border communications) of the Private Sector Act. Importantly, Step 2 does not recast PIAs as a substitute for inventorying, nor does it expand their statutory scope. Rather, PIAs are presented as inputs that inform and support a broader, organization‑wide mapping of personal‑information processing activities.
Although the Guide does not refer to records of processing activities (“ROPA”) by name, the breadth, structure, and level of detail contemplated by Step 2 resembles, in practical terms, a ROPA under article 30 of the European Union’s General Data Protection Regulation (“GDPR”). Unlike the GDPR, Quebec law does not impose an express obligation to maintain a ROPA. Outside of the specific PIA requirements tied to projects and cross‑border disclosures, the Private Sector Act does not mandate a comprehensive, organization‑wide documentation of processing activities.
That said, the Guide suggests that, beyond assessing privacy risks on a project‑by‑project or transfer‑specific basis, a global inventory of personal‑information processing is a prudent component of an organization’s security posture. In this sense, Step 2 points toward a ROPA‑like exercise not as a formal compliance requirement, but as a useful and defensible security measure in support of the general obligation under article 10 to implement reasonable security measures for the protection of personal information.
For organizations already maintaining a ROPA for GDPR purposes, that documentation may serve as a strong starting point for the Step 2 inventory, provided it is adapted to Quebec‑specific concepts such as confidentiality incidents, risk of serious injury, unique PIA requirements, and the lifecycle factors emphasized in article 10.
Recommended security measures (Step 4)
In Step 4, the Guide details the types of measures organizations should consider once risks have been identified. Considering that the guidance is only available in French, we prepared the following unofficial translation of the security measures enumerated in the Guide.
Administrative and organizational measures
Governance measures
- Ensure that privacy policies and practices are up to date (e.g., data retention and destruction policy, contract management processes that protect personal information);
- Form an information security and privacy committee comprising individuals who play a strategic role within your organization and report to senior management;
- Clearly communicate your expectations to staff;
- Report periodically to senior management;
Tactical measures
- Train and educate staff (e.g., strong passwords, risks associated with malware or social engineering, or clean desk principles);
- Develop an annual action plan for adding security measures;
- Actively monitor the effectiveness of the measures deployed;
Operational measures
- Grant access rights to personal information only to staff whose duties require such access (i.e., least privileged access);
- Depending on the size of your company, train respondents who can advise their colleagues on specific security measures;
- Develop standard templates (e.g., personal information collection form, confidentiality agreement, non-disclosure agreement, contractual clauses) and review them periodically; and
- Use robust identification protocols.
Physical measures
- Control access (e.g., offices, server rooms, wiring rooms, alarm systems); and
- Restrict access to premises or filing cabinets where paper documents containing personal information are stored.
Technical measures
- Promote strong usernames and passwords;
- Ensure encryption of communications and stored information;
- Encrypt mobile devices;
- Implement a firewall;
- Ensure network perimeter defense;
- Depersonalize information before use when the identity of individuals is not necessary for the intended processing;
- Ensure effective management of employee access to personal information, log such access, and use the logs to detect irregular situations;
- Systematically apply software updates;
- Block USB ports;
- Adopt a document management system; and
- Implement means for the secure destruction of personal information.
The above is our unofficial English translation of the security measures found on pages 10 and 11 of the Guide.
While the Guide and Checklist do not create new legal requirements, they offer important insight into how the CAI expects organizations to think about prevention under the Private Sector Act. In particular, the emphasis on inventorying personal information, assessing risk in context, and selecting proportionate safeguards reflects a mature, risk‑based reading of article 10.
The guidance also makes clear that preventing confidentiality incidents is an organization‑wide responsibility that must be revisited over time as activities, technologies, and risk profiles evolve. From a practical standpoint, any organization doing business in Quebec should assess whether its existing policies, procedures, and safeguards are aligned with the CAI’s guidance. Where gaps are identified, organizations should consider adjusting their practices accordingly and, critically, documenting their decisions and controls. In an accountability‑driven regulatory environment, organizations must be prepared to demonstrate how their safeguards were selected, implemented, and reviewed, particularly in light of CAI guidance.
To learn more about how our Cyber/Data Group can help you navigate the privacy and data landscape, please contact national co-leaders Charles Morgan and Daniel Glover.
[1] See articles 90.12 and 91 of the Private Sector Act.
[2] See article 93 of the Private Sector Act.
[3] See articles 90.1 and 91 of the Private Sector Act.
Stay Connected
All form fields are required "*"




